TL;DR: In this blog post I’m going to write about my personal experience about the Offensive Security Exploitation Expert (OSEE) certificate and the Advanced Windows Exploitation (AWE) training; delivered in Las Vegas at BlackHat USA 2019.
0x01: Introduction
After I’ve passed the OSCP in December 2017 and the OSCE in July 2018, I’ve decided to improve my exploitation skills especially with the focus on Windows and modern memory protection techniques such as ASLR, DEP, SMEP, CFG, and ACG. These bunch of techniques are state of the art and enabled by default on modern Windows installation. People who know me, already know that “Try harder” is not just a slogan in my life, this was one reason why the AWE was my preferred option.
In my opinion, the official description covers all that I’m looked for: [1]
Writing exploits on modern Windows based platforms over the years has become a complex dance of memory manipulation to circumvent modern mitigations Microsoft has put in place. Offensive Security’s Advanced Windows Exploitation Techniques (AWE) challenges you to develop creative solutions that work in today’s increasingly difficult exploitation environment. Covering techniques ranging from precision heap reallocation, to DEP, ASLR, CFG, and ACG bypass, virtual machine escape, real-world 64-bit kernel exploitation and sandbox escape, in a hands-on lab focused environment, AWE makes a point of introducing a concept and then allowing you to work through a case study applying what you learned, with multiple instructors on hand for help with any problems. The case studies covered include vulnerabilities discovered by our research team or exploits written by Offensive Security.
Everyone who had already the pleasure to take an Offsec exam knows what “Try harder” means. This is what Offensive Security says about AWE:
This is the hardest and most intense Offensive Security course we offer and requires a lot of commitment from the students
The AWE is the hardest course Offensive Security offers. And trust me it was not a lie.
0x02: Registration
Unlike the other courses offers by Offsec this course is only available onsite which means, that the course is sold out in a blink of an eye. There are some rumors outside that the course will be going online this year but to be honest I guess this course will never go online. In my opinion the reason for this is quite simple, the course is always up-to-date and will be updated every year. As a result, making new videos and resources is a lot of work, furthermore, due to the fact that this course is advanced and the topic covers by this course is complex - it is really good to have an instructor that can help.
As I mentioned before, this course is sold out in a blink of an eye, for this purpose I’ve built a bot that crawls all necessary information and pushed me a message via mail, push notification and SMS directly when the registration opened. The reason why SMS and the whole stuff is very simple. I travel by train and the internet connection in Germany during a train ride is not well-known as super fast.
However, to be 100% sure that I never miss any information my bot used different approaches:
- Crawled the official BlackHat/Offsec site for any information;
- Looked if the registration and training plan is open and published; and
- If Offsec and BH are twitter about the AWE training;
Furthermore, I already know from the last BlackHat news that the registration is going to start around mid or end of January.
Luckily my bot worked like a charm and kicked in after the registration was open. The AWE course was sold out in less than 30 minutes [2]:
#BlackHat Vegas trainings have opened for registration, and turns out AWE sold out in less than 30 mins!
— Offensive Security (@offsectraining) January 24, 2019
Sign up for AWAE and PWK before they sell out as well! https://t.co/RaOqza41i4
And before you ask, no, we can’t slip you in. Black Hat handles all registration.
0x03: Challenge
Approximately a month before the course started in Vegas, Offsec sent a small challenge to everyone who was able to get a seat in this course. This challenge was not really hard in my opinion. The purpose of this challenge was to help to get warmed up and to ensure that the attendee has the minimal technical prerequisites required for the course at Black Hat.
0x04: Training
The training itself goes 4 days but it is actually designed for 5 days this means that the training hours in Vegas were extended every day until the room cleaner come into the room and kicked us out. As a result, every day was approximately 10h long from 9 a.m. to 7 p.m. In addition, there were some extra miles that could be solved after the training days.
Day 1: Shellcode/VMWare Module
The first day started with an introduction to shellcoding on 64bit systems as well as a custom shellcode followed by a case study of a VMWare guest escape through a UAF bug. This chapter covers also bypass techniques like DEP and ASLR. After we were able to understand the bug and the underlying used heap mechanism and how we can trigger the bug as well we used a memory leak to bypass ASLR.
Day 2: VMWare/Edge Module
The second day started by using the ASLR bypass to calculate the necessary addresses. With this knowledge, we build a ROP chain to gain code execution and bypass DEP. After successful exploitation and access to the host system, we used the custom shellcode from day one to execute arbitrary code on the host system. We also bypassed the Windows Defender Exploit Guard (WDEG). This is a replacement of EMET in the Windows 10 Fall Creators Update.
After a long night, I was able to build a ROP chain to disable DEP and execute the calculator on the host system.
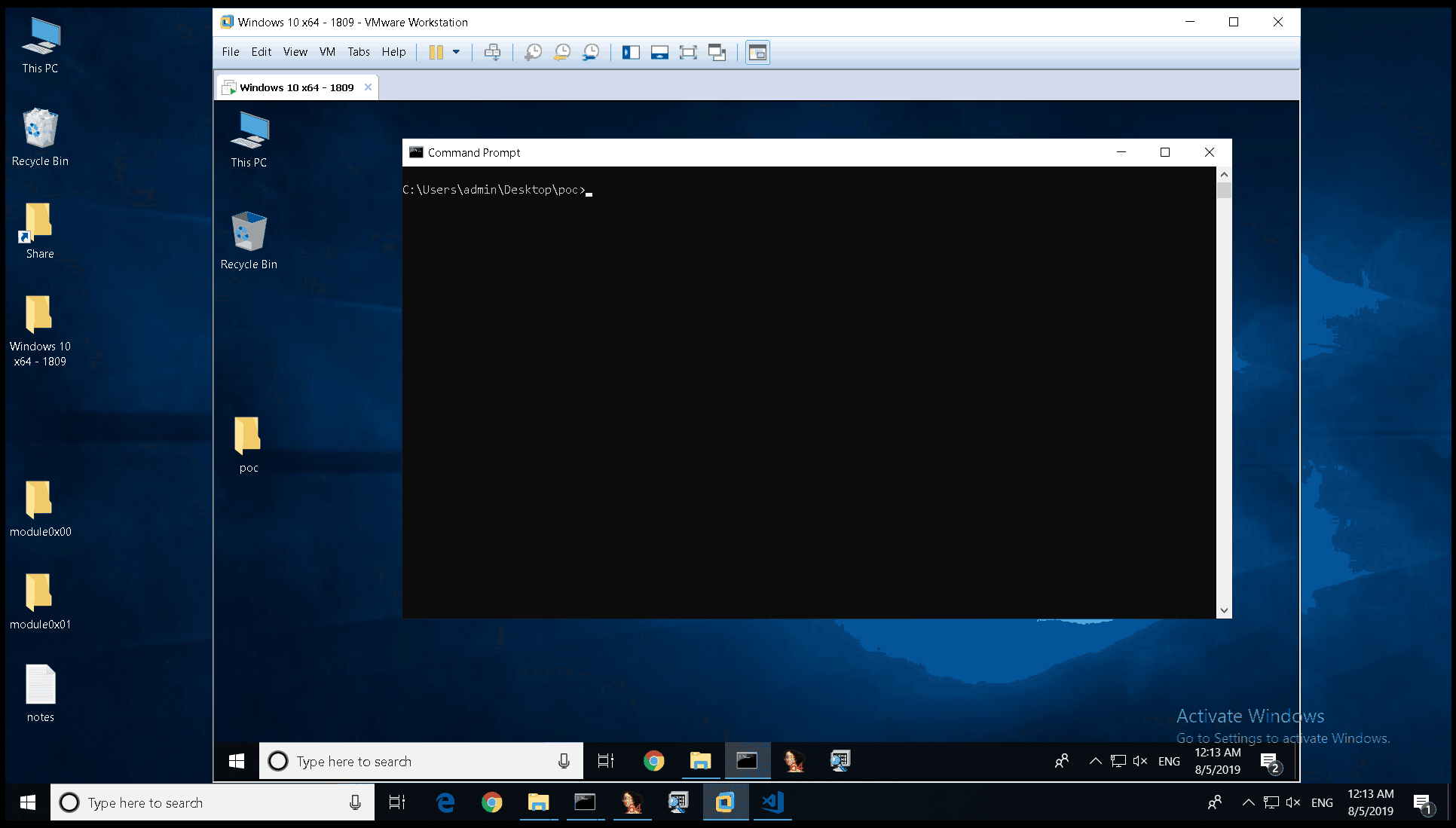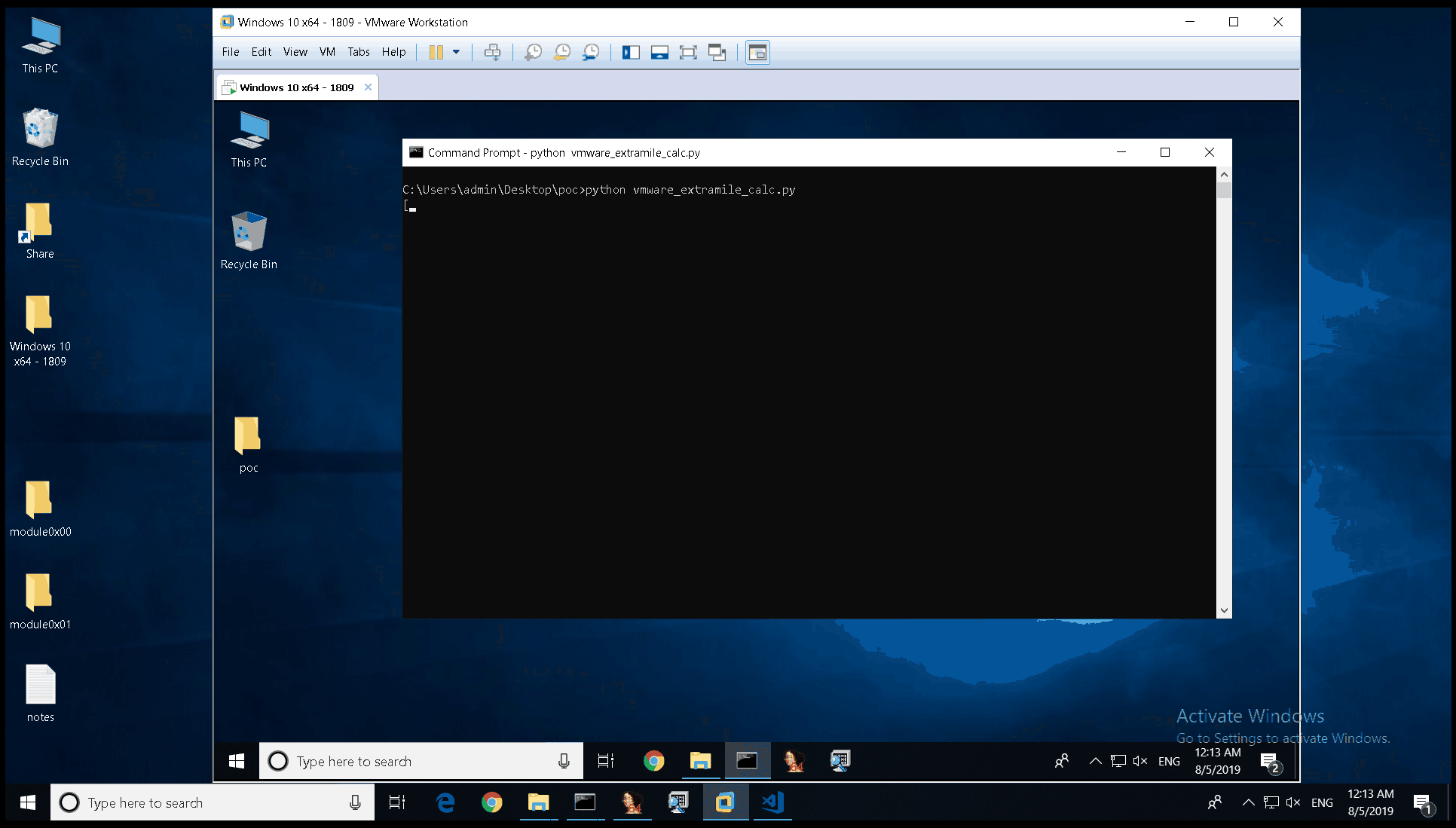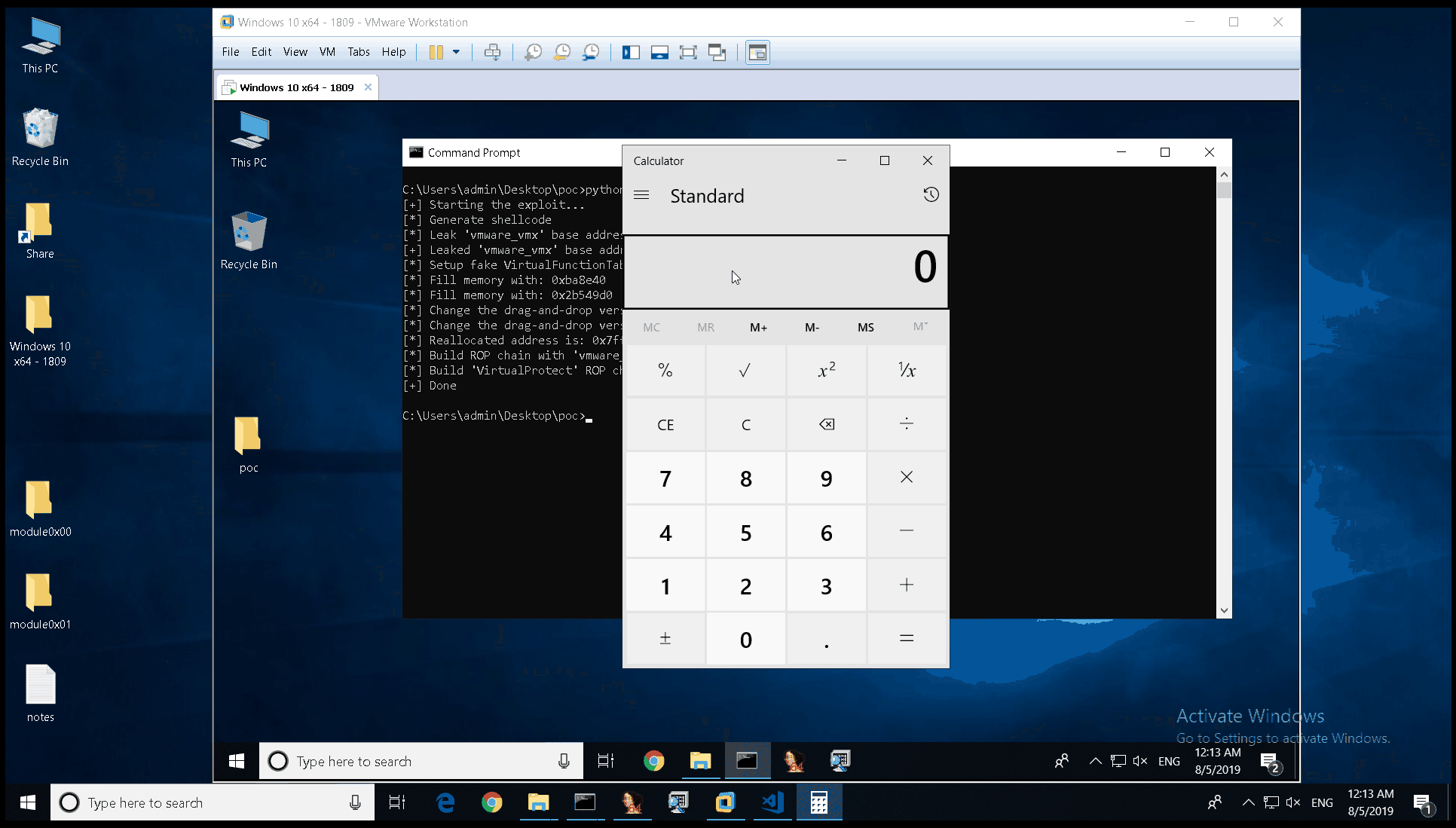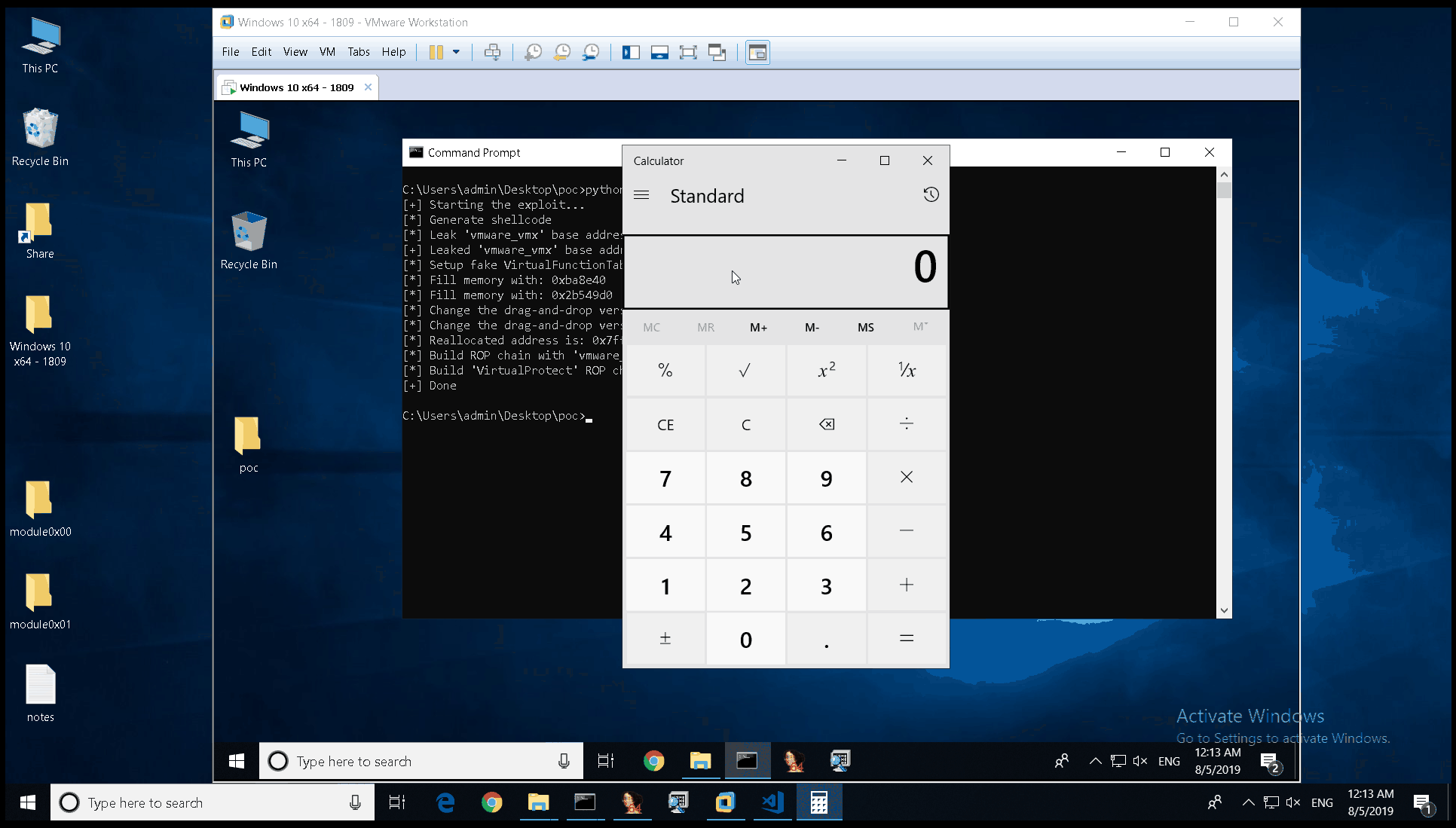
The second half-day, we started with the behavior of JavaScript on 64bit systems
followed by a case study of a Type Confusion bug in Microsoft Edge found by the
Google Project Zero team (CVE-2017-8601).
Offsec showed how we can use this kind of bug class to gain the read/write
primitive and eventually we were able to bypass ASLR by leaking a pointer to
Chakra.dll.
Day 3: Edge Module
From my point of view, the third day was the hardest one. After we had leaked a
pointer in Chakra.dll and bypassed ASLR we also had to bypass two new
protection called Control Flow Guard (CFG) and Arbitrary Code Guard
(ACG). We bypassed CFG by overwriting a return address on the stack and
taking the control of the instruction pointer. ACG was bypassed by
duplicating the handle to another instance of the “MicrosoftEdge.exe”
(the JIT process) where ACG was disabled. For this purpose, we build a
ROP chain that copied an ROP chain from the rendering process to the
JIT process where ACG was disabled. The copied ROP chain is going to
bypass DEP in the JIT process and archive code execution. From this
point we escaped the sandbox protection by exploiting a kernel vulnerability in
the win32kfull.sys driver to get a shell with SYSTEM privileges.
Day 4: FortiNet Module
On the last day, we started with 64bit kernel driver exploitation. In this module, we learned how a kernel driver interacts and how we can communicate with the driver. Furthermore, how privilege levels on Windows work and how we can steal a token from a SYSTEM process. Followed by a case study of an arbitrary function overwrite in FortiClient Antivirus (CVE-2015-5736) found by Core Security.
In addition, Offsec gave us an introduction to memory paging and structures.
This knowledge’s helps to bypass the Supervisor Mode Execution Prevention
(SMEP). SMEP prevents the transfer of execution control from kernel
space to user space. To execute the exploit later with a low integrity user we
used CVE-2015-4077
to leak the base address. This step was necessary because it is not possible to
use API’s like EnumDeviceDrivers or NtQuerySystemInformation to get the
base address ntsokrnl with a low integrity user. After we were able to get
the base address of ntoskrnl we were able to build a ROP chain to
bypass SMEP. After SMEP was bypassed we were able to execute the token
stealing payload and got a privileged shell.
0x05: Exam
The exam in total goes 96 hours (72h for the practical part and another 24h for writing the report). In this 72h you have to solve 2 challenges, one challenge can be solved in two different ways which get different points, depends on which way the challenge will be solved. The second challenge gives the most points. Just like other Offsec exams, I can’t tell too much about the challenges and the exam itself. From my point of view, this exam is much more difficult and time consuming compared to OSCP and OSCE and all skills learned in the training is needed to pass the exam.
During my preparation for the exam, I’ve built a few exploits for different bug classes especially on kernel drivers and I spent a lot of time in WinDBG and IDA. Luckily, during this time I’ve found some 0day’s in kernel drivers from different vendors such as Biostar and ASUS (CVE-2019-17603). Long story short; I was able to solve both challenges in approximately 30h with a 2x 6h nap. The rest of the hours I’ve used to collect all necessary data improved my exploit and ensured that all data are in place for the later report. These steps were really important because Offsec wanted all little pieces of code/steps and approaches that I’ve used to solve the challenges. It was a lot to document; in the end, my final report included a lot of information and was 62 pages long. After a week that I’ve submitted my report to Offensive Security I got an email with my result that I had smashed the exam :).

0x06: Final thought
I had a lot of fun during the training in Vegas as well as in the exam. I can highly recommend this training. For everyone that is interesting in my preparation, I’ve created a GitHub repo [3] with a list of resources and Kernel exploits.
0x07: Resources
-
[1]
BlackHat USA 2019 - Course Description - https://www.blackhat.com/us-19/training/schedule/#advanced-windows-exploitation-14403
-
[2]
Offensive Security Twitter Channel - https://twitter.com/offsectraining/status/1088535960655196168
-
[3]
GitHub Repo - OSEE - https://github.com/dhn/OSEE